All About Sharepoint Data Migration
Monitor for compliance: Screen the Share, Point Online setting for conformity with data personal privacy, protection, as well as governance plans and also requirements. Assess and optimize the search: Assess and maximize the search functionality in Share, Factor Online to guarantee that users can quickly locate and also access the migrated information as well as content - sharepoint data migration. Strategy for mobile access: Prepare for mobile accessibility to the migrated data as well as material, making sure that individuals can access it from anywhere, anytime, on any kind of device.
Prepare for data movement: Prepare for information migration to other systems or systems as needed, taking into account the movement objectives, scope, and also needs. Prepare for recurring support: Prepare for continuous assistance and also upkeep, including updating, patching, and dealing with any type of concerns that might develop in time. Make sure data privacy and also protection: Guarantee that the migrated information and web content are shielded versus unapproved access, breaches, and other safety and security threats.
Sharepoint Data Migration - An Overview
By keeping these 25 ideal methods, on your radar, you can guarantee that the movement is smooth, reliable, as well as straightened with the company's objectives and requirements, as well as that the moved information as well as material are secure, obtainable, as well as took care of in accordance with best practices.
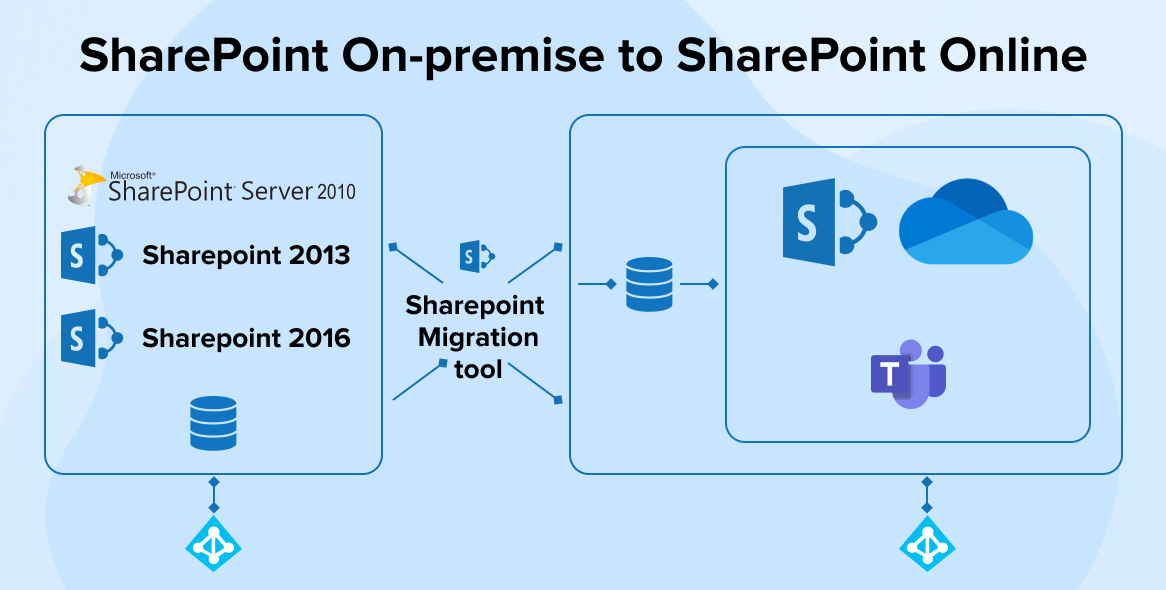
Migrating to Share, Factor Online can be a complex process and selecting the appropriate migration device is critical to make certain a smooth and effective transition. Here are some pointers to aid you pick the ideal device for your Share, Factor movement: When comparing Share, Point movement devices like Mission device, Sharegate device, Share, Point Movement Tool (SMAT), Metalogix Content Matrix, Ave, Point Migration Device, and Bit Titan Migration, Wiz, it is necessary to think about elements such as attributes, simplicity of use, supported platforms, efficiency, as well as cost.
Parameters, Mission tool Sharegate device Share, Factor Movement Tool (SPMT) Metalogix Material Matrix Ave, Point Movement Device Bit, Titan Migration, Wiz Types, Cloud Base Non-Cloud Base Non-Cloud Base Non-Cloud Base Non-Cloud Base Cloud Base, Interpretation, Pursuit tool may describe several products used by Pursuit Software, each with its own set of features as well as abilities. sharepoint data migration.
10 Easy Facts About Sharepoint Data Migration Described
Attributes, Provides computerized analysis, material mapping, organizing, and sustains Supports migration from numerous sources, pre-migration evaluation, web content mapping, and scheduling. Free movement device offered by Microsoft, sustains migration from on-premises Share, Point websites, data shares, and also various other cloud storage carriers. Provides automated discovery, pre-migration assessment, metadata mapping, as well as granular material movement.
Sustains movement from numerous resources, pre-migration evaluation, information mapping, as well as organizing. Scalability, Handles massive and also intricate movements efficiently. Ideal for both basic as well as complicated movement jobs. Share, Factor sites, data shares, as well as various other cloud storage space suppliers. Appropriate for large and also complicated migration jobs. Recognized for scalability as well as managing complicated movements.
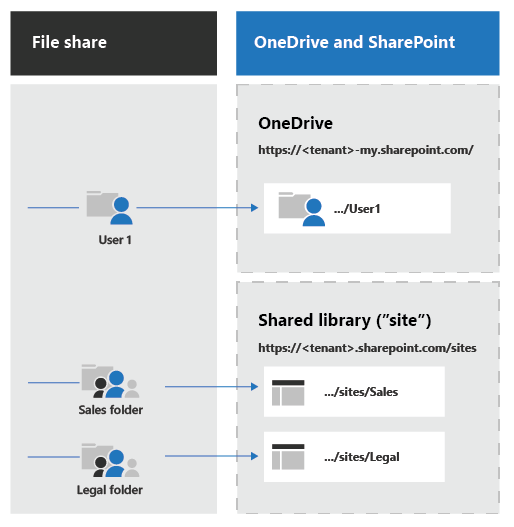
Offers an user-friendly user interface. Provides a thorough interface Provides an user-friendly interface. Supported Movement Scenarios Moves from Share, Factor on-premises, data shares, as well as other partnership platforms to Share, Factor Online.
Migrates from different resources, including Share, Point on-premises, documents shares, Exchange Public Folders, and also various other collaboration platforms to Share, Point Online. Migrates from different sources to Share, Point Online.
Some Ideas on Sharepoint Data Migration You Need To Know
Constraint It might have constraints in dealing with complex migration scenarios and unable to migrate customized list like study listing. It might have restrictions on migration rate. It may have restrictions in taking care of complicated migration scenarios and personalization demands. It might have a steeper knowing contour as well as a higher price point compared to various other devices.
There are some restrictions on the file size that can be migrated at one shot. At Netwoven, we have efficiently implemented over 100 of such movement projects from Google work space, M365, Microsoft On-Prem Infrastructure to M365 spanning over greater than a years in various Tier 1 industry segments. Our experience recommends that there is nobody tool that fits all.
We have actually had the ability to establish a set of multiple-use devices for material supply analysis, movement mapping, movement testing and audit. Below is a sample a fantastic read photo of among our devices that enables the customer to quickly flag the migration options for any material in the resource. These tools enhance all the above and also can prove to be handy for any kind of movement job undertaken (sharepoint data migration).